Cybersecurity
Our Cybersecurity services are based on leading industry standards and involve experts, processes, technology and infrastructure.

Cybersecurity
Our Cybersecurity services are based on leading industry standards and involve experts, processes, technology and infrastructure.
Cybersecurity


PLATFORM - CYBERSECURITY
End-to-end protection of your company’s information and assets
End-to-end protection of your company’s information and assets
No matter where the IT resources are located, Axity provides a comprehensive Cybersecurity process, which guarantees end-to-end protection of your company’s information and assets.
Our Cybersecurity services are based on the main industry standards and involve experts, processes, technology and infrastructure. All these components operate in a comprehensive way to achieve a proactive management of your Cybersecurity.

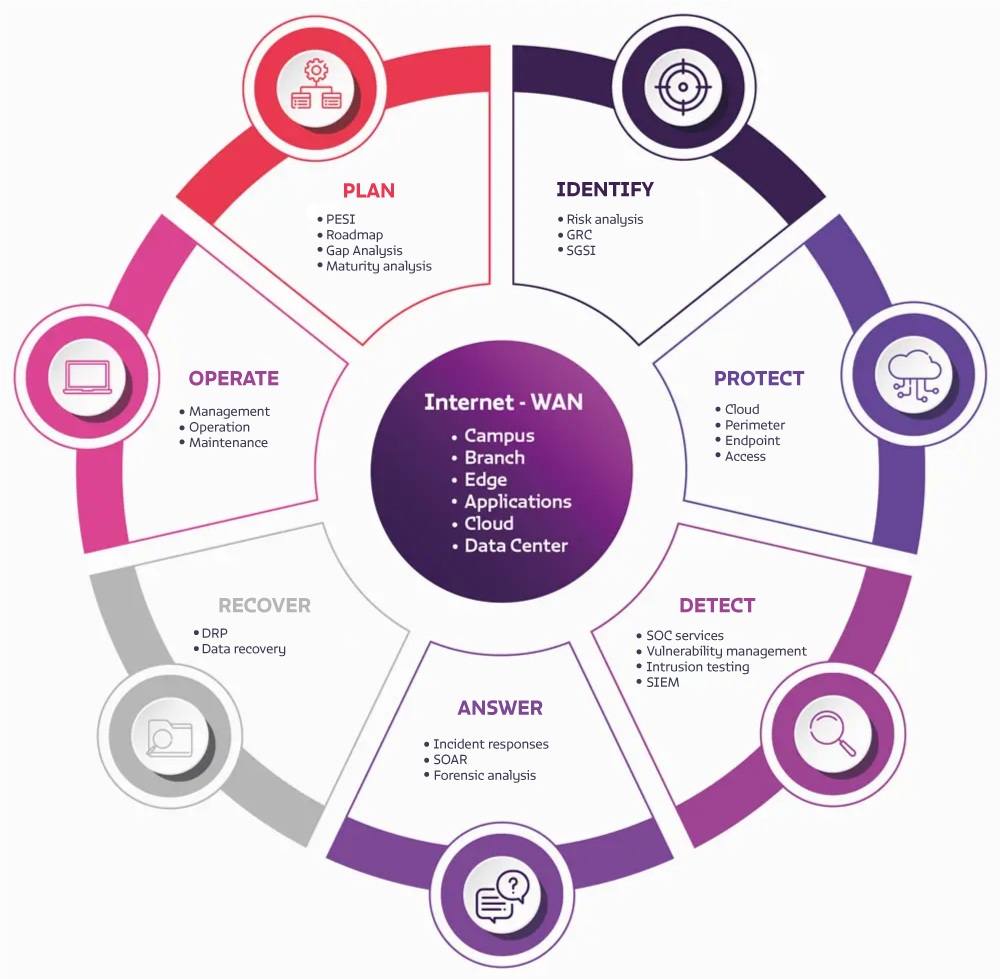
We implement a strong Cybersecurity strategy
We implement a strong Cybersecurity strategy
We have a wide range of products and services needed to implement a robust Cybersecurity strategy:
- Plan: goals, metrics, actions, infrastructure and talent.
- Identify: risk points.
- Protect: protection technology.
- Detect: detection technology.
- Respond: incident response strategy.
- Recover: operation and information.
- Operate: your entire cybersecurity process.
Cybersecurity products and
services
- CLOUD protection.
- Perimeter protection.
- EndPoint protection.
- Remote access protection.
- Server protection.
- Network protection.
- Protection of IoT and TO.
- Protection of Applications.
- SIEM Platform.
- SOAR Platform.
- Platform Vulnerabilities.
- Platform Administration
- SOC Services
- Monitoring
- Correlation
- Vulnerability Management.
- Incident Management.
- Automatic Response (SOAR).
- Threat Intelligence.
- Brand Monitoring.
- Internal Threats.
- Gap analysis (regulations)
- ISMS implementation
- Risk analysis and management
- PESI
- Security RoadMap
- Security Governance
- DRP Definition / Implementation

Cybersecurity products and
services
- CLOUD protection.
- Perimeter protection.
- EndPoint protection.
- Remote access protection.
- Server protection.
- Network protection.
- Protection of IoT and TO.
- Protection of Applications.
- SIEM Platform.
- SOAR Platform.
- Platform Vulnerabilities.
- Platform Administration
- SOC Services
- Monitoring
- Correlation
- Vulnerability Management.
- Incident Management.
- Automatic Response (SOAR).
- Threat Intelligence.
- Brand Monitoring.
- Internal Threats.
- Gap analysis (regulations)
- ISMS implementation
- Risk analysis and management
- PESI
- Security RoadMap
- Security Governance
- DRP Definition / Implementation

We have the best partners
to protect your business
We have the best partners
to protect your business
- Prisma Cloud: detects risky configurations, identifies threats, suspicious behavior, malware, data leakage and vulnerabilities.
- Prisma Access: protects access regardless of the place of origin or location of resources.
- Strata Firewalls: network protection, DC, internet access. Filters traffic coming from internal or external networks.
- Cortex XDR: extended detection and response, integrates network, endpoint and cloud data to stop sophisticated attacks.
- Cisco ISE: control device access to the corporate network, ensuring that only authorized devices access network resources.
- Umbrella: protects users and endpoints from threats on the Internet, regardless of their location. Allows complete visibility of users’ browsing activity.
- StealthWatch: security analytics and visibility solution that leverages enterprise telemetry from existing network infrastructure. Provides advanced threat detection, accelerated threat response and simplified network segmentation through the use of machine learning.
- Update management: centrally manage the patching of Windows servers.
- Azure Security: protect SaaS applications against all types of threats and unauthorized access attempts.
- Sentinel: correlation, security log analysis and immediate response solution for SOC functions.
- Tenable SC: Collects and evaluates vulnerability data across multiple Nessus® scanners distributed throughout your enterprise. Illustrates vulnerability trends over time to assess risk and set priorities.
- Tenable IoT: vulnerability scanning from the cloud, including web application scanning.
- Balancers: solution for balancing and distributing loads to internal application servers.
- WAF: protects web applications from specific attacks on these applications.
- PAM: solution to protect passwords from privileged access and control the actions that privileged users perform on the platform.