Cloud Security
Avoid risks and attacks in the security of Cloud environments.

Cloud Security
Avoid risks and attacks in the security of Cloud environments.
Cloud


CYBERSECURITY - CLOUD SECURITY
Decreases exposure to digital threats in the cloud
Decreases exposure to digital threats in the cloud
The decentralization of data and the incremental adoption of the use of private and public clouds generate digital risks that must be managed for each component within and with the cloud in order to reduce exposure to digital threats.
As a result, organizations must complement their security strategies to meet the Cloud needs that vary according to the organization, industries, assets and data that must adapt to the speed required by the business, this challenge requires the design and implementation of controls to maintain adequate objective security to get the most out of cloud capabilities, applying criteria such as security by design, least privilege to identities and Zero Trust “never trust, always verify”.
At Axity we provide multi-Cloud security services, in conjunction with other Cloud capabilities, to generate confidence to organizations by protecting their assets and providing users with access to the organization’s resources, maintaining adequate security levels in balance with their usage experience.


Cloud Security services services allow:
Cloud Security services services allow:
- Manage, Operate and Monitor (SOC, Security Operation Center) security services in public Cloud.
- Architecture and design of Cloud Security components (DDoS, CASB, SASE, etc.).
- Security assessment to identify/measure Cloud controls.
- Ensure compliance and ScoreCard of public cloud security risks.
Discover the benefits of benefits of having a cybersecurity Cybersecurity services in the cloud
Discover the benefits of benefits of having a cybersecurity Cybersecurity services in the cloud
- Mitigates exposure and failure times due to digital threats in the Cloud. Ex: Cryptomining, Ransomware, etc.
- Monetize the efficiencies of Cloud vs On-premise solutions.
- Generate business metrics based on Cloud security posture.
- Update organizational guidelines and policies for unified Cloud governance.

Cloud Security
We implemented a solid solid Cybersecurity strategy
We implemented a solid solid Cybersecurity strategy
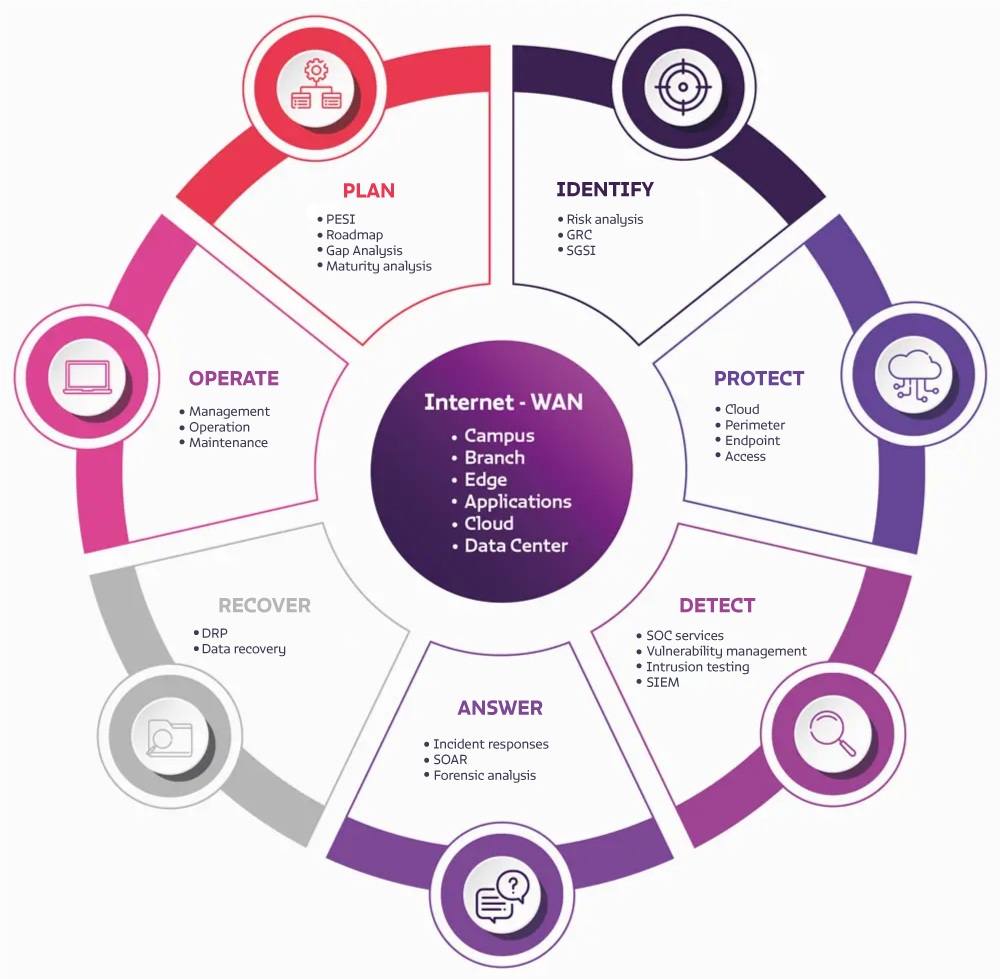
We have a wide range of products and services needed to implement a solid Cybersecurity strategy:
- Plan: goals, metrics, actions, infrastructure and talent.
- Identify: risk points.
- Protect: protection technology.
- Detect: detection technology.
- Respond: incident response strategy.
- Recover: operation and information.
- Operate: your entire cybersecurity process.
Technology partners






Secure your information in the cloud
with our Cloud Security service. .
Complete the form and download the ebook "12 fundamental steps that strengthen cybersecurity in your organization".
Secure your information in the cloud with our Cloud Security service.
Complete the form and download the ebook "12 fundamental steps that strengthen cybersecurity in your organization".