Offensive & Security Testing
Implements mitigation measures for findings that arise from identifying security breaches and vulnerabilities early on from an attacker's perspective.

Offensive &
Security Testing
Implement mitigation measures for findings that arise by identifying security gaps and vulnerabilities early from an attacker's perspective.


Security Testing
Offensive & Security Testing
Anticipate cyberincidents and implement mitigation measures
Anticipate cyberincidents and implement mitigation measures
Organizations must know the risks associated with their assets to have a security posture that anticipates a cyber incident and be able to implement mitigation measures for the findings that arise when identifying security breaches and vulnerabilities early, optimizing the organization’s resources based on prioritization and potential impact.
At Axity we have the capabilities and experience in RedTeam services and offensive security, which allows through a group of trained and certified specialists, to perform security exercises from the perspective of an attacker and to measure in a real way the level of maturity of the organization from the digital and human point of view.


Offensive & Security Testing services Security Testing services allow
Offensive & Security Testing services Security Testing services allow
- Offensive security and ethical hacking: identify the degree of exposure of an organization.
- Vulnerability management: define, identify, classify and prioritize weaknesses to IT infrastructure.
- Cybersecurity awareness programs: assess and identify the degree of organizational culture in cybersecurity.
- Digital forensics: identify, preserve, analyze and present valuable data generated during an event or incident.
Learn more about the benefits of our Offensive & Security Testing service.
Learn more about the benefits of our Offensive & Security Testing service.
- Minimize the impact of a possible cyber attack.
- Identify real cybersecurity risks.
- Assess your team’s ability to respond to incidents.
- Continuous evaluation of security against any type of attack.
- Know what were the methods and digital activities used in a digital incident.
- Acquire digital evidence through information preservation techniques.
- Analyze the events occurred while maintaining a chain of custody.

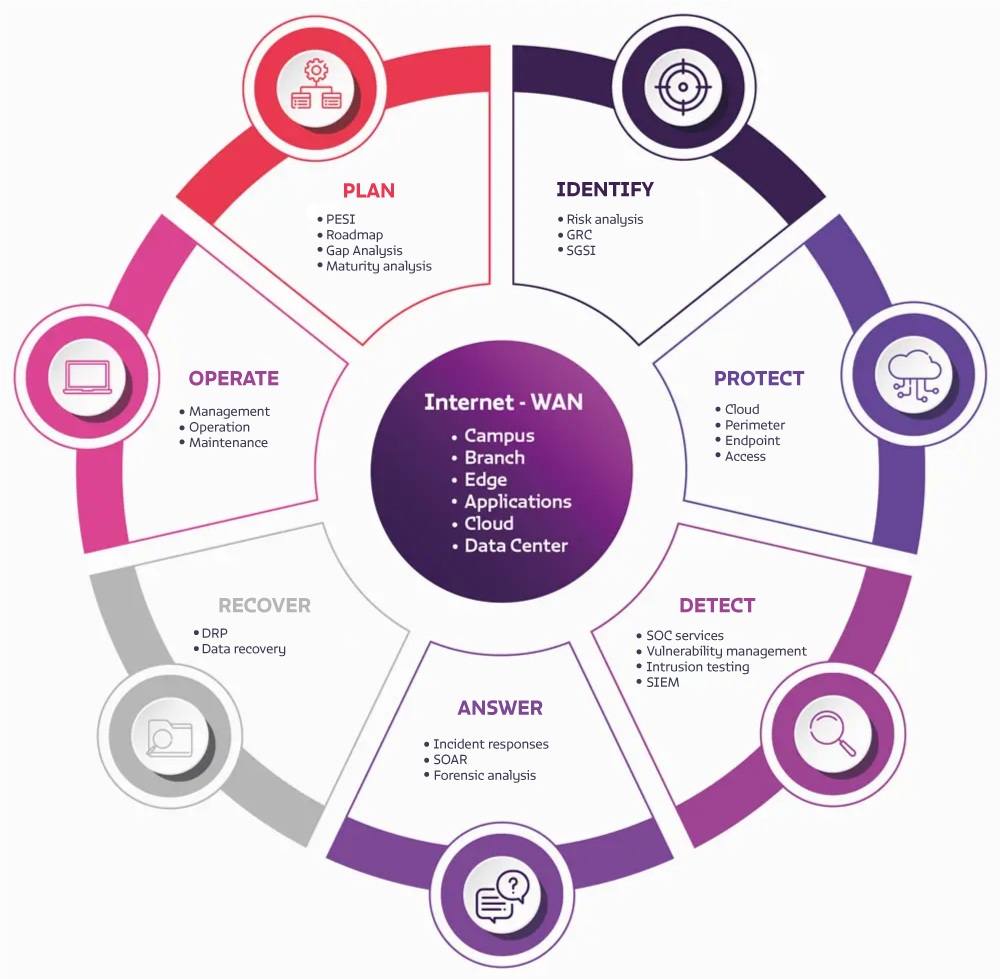
We implemented a solid solid Cybersecurity strategy
We have a wide range of products and services needed to implement a solid Cybersecurity strategy:
- Plan: goals, metrics, actions, infrastructure and talent.
- Identify: risk points.
- Protect: protection technology.
- Detect: detection technology.
- Respond: incident response strategy.
- Recover: operation and information.
- Operate: your entire cybersecurity process.
Technology partners
Offensive & Security Testing






With Vulnerability Management Offensive & Security Testing you implement mitigation measures for findings from an attacker's perspective.
Complete the form and download the ebook "12 fundamental steps that strengthen cybersecurity in your organization".