Security as a Code
Maintain the security of data and information from the development of your new digital products.

Security As a Code
Maintain data and information security from the development of your new digital products.


As a Code
SECURITY AS A CODE
Security as a Code: security in software development
Considering security by design is an efficient methodology that is being adopted more frequently in software development practices and IT operations within organizations. Maintaining data security, in emerging technology scenarios, is a challenge that requires the integration of development, IT operations and security teams while generating products / services that allow organizations to be competitive, optimizing costs and using innovation as a business accelerator. In Cloud, Serverless, Infrastructure as a Code scenarios, agile security is also required.
At Axity we enhance the capabilities of agile and traditional development teams with guidelines, services and security products, to ensure not only the functional results of the piece of software being developed, but also its security, to generate confidence in the final product (Security as a Code / DevSecOps).

Security as a Code services services allow:
Security as a Code services services allow:
- Assessment of security practices in development teams (As Is) (To be).
- Training in good development practices, OWASP, NIST, etc.
- Security architecture in software components.
- Static code analysis services (SAST) and dynamic analysis of applications (DAST).
- Monitoring services with correlation solutions.
Learn about the benefits of Security as a Code
- Generate confidence in the pieces of software made.
- Cost efficiency by mitigating vulnerabilities in the early stages of the development life cycle (SDLC).
- Provide security capabilities to development teams.
- Agile deliveries considering security from the design stage.

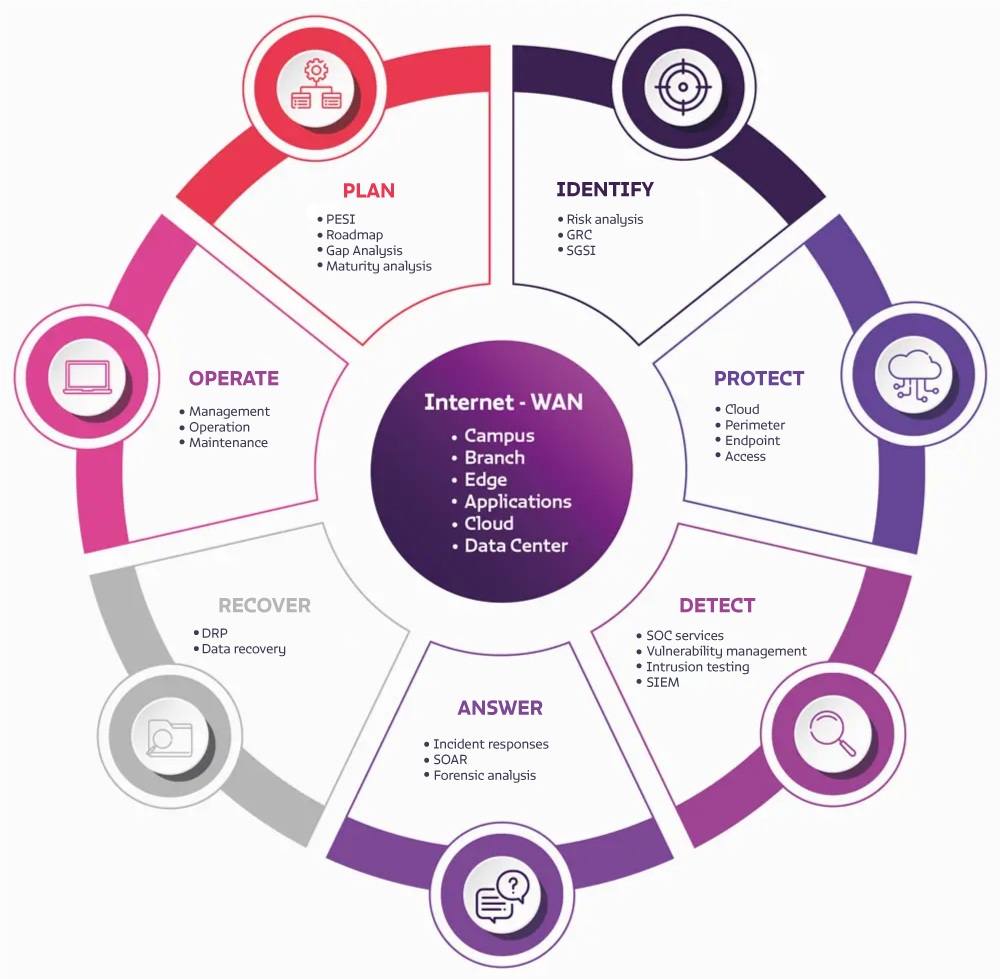
We implemented a solid solid Cybersecurity strategy
We have a wide range of products and services needed to implement a solid Cybersecurity strategy:
- Plan: goals, metrics, actions, infrastructure and talent.
- Identify: risk points.
- Protect: protection technology.
- Detect: detection technology.
- Respond: incident response strategy.
- Recover: operation and information.
- Operate: your entire cybersecurity process.
Technology partners






With Security as a Code, keep your digital products and services secure, in an agile way, from their design and development.
Complete the form and download the ebook "12 fundamental steps that strengthen cybersecurity in your organization".