360º Digital Security
Architecture, provisioning, implementation, configuration, migration and deployment of the security platform in your company.

360°
Digital Security
Architecture, provisioning, implementation, configuration, migration and start-up of the security platform in your company.

Digital Security
CYBERSECURITY • 360 º DIGITAL SECURITY
The evolution of technology and cybersecurity
The evolution of technology and the digitalization of organizations, leads to continuously maintain the implementation of technological controls according to the protection needs of each organization; this has led companies to face great challenges in the proper selection of security solutions for the diversity of the market, these challenges become more complex by requiring specialized personnel to obtain the maximum benefit from the acquired solution. Thus, technology, design, human talent and methodological processes are criteria that must be taken into account when selecting and implementing security solutions.
At Axity, we have capabilities and experience in different Cybersecurity technologies, providing value from the analysis stage to the design based on the requirements of the business and current technology that your organization has; from this analysis we propose the architecture, provisioning, implementation, configuration/migration and implementation of the security platform and its associated components.

Cybersecurity 360

The architecture services and implementation of cybersecurity allow for:
- Analysis of requirements and current situation.
- Design and architecture.
- Provision, implementation / configuration / migration of Cybersecurity solutions.
- Functionality testing and production start-up.
- Support.
- Preventive and corrective support.
Discover all the benefits of having our 360º Digital Security service.
- To have security platforms according to the business needs.
- Correct integration with the current and future technological environment of the organization.
- Guaranteed implementation with the highest standards and best practices.
- Provide confidence to the organization with its digital initiatives.

Digital Security
We implemented a solid solid Cybersecurity strategy
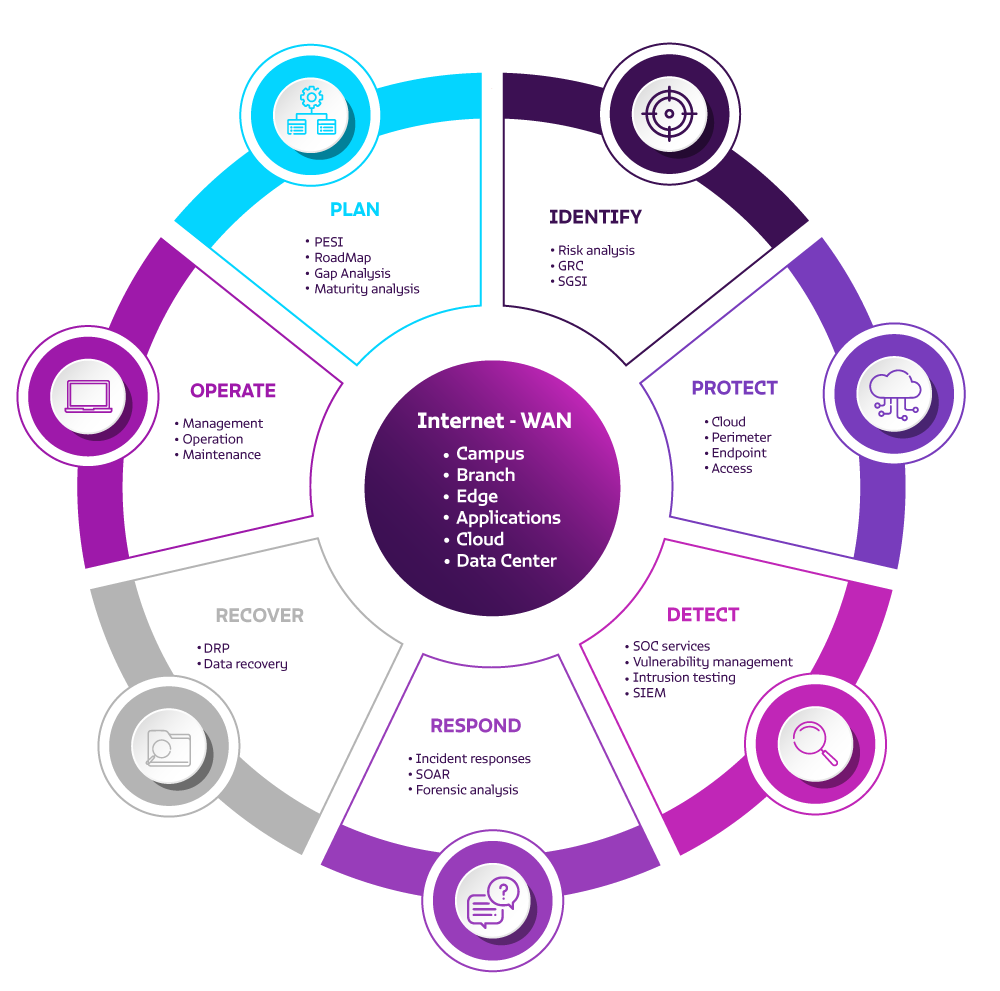
We have a wide range of products and services needed to implement a solid Cybersecurity strategy:
- Plan: goals, metrics, actions, infrastructure and talent.
- Identify: risk points.
- Protect: protection technology.
- Detect: detection technology.
- Respond: incident response strategy.
- Recover: operation and information.
- Operate: your entire cybersecurity process.
Cybersecurity 360
Technology partners






Cybersecurity
Implement and integrate the cybersecurity technology platform that your company needs.
Complete the form and download
the ebook "12 fundamental steps that strengthen cybersecurity in your organization".