Governance, Risk & Compliance
Establishes a security governance framework based on regulatory frameworks and best practices to align responsibilities, processes and guidelines, adequately managing digital risks.

Governance,
Risk, &
Compliance
Establishes a security governance framework based on regulatory frameworks and good practices to align responsibilities, processes and guidelines, properly managing digital risks.
Risk & Compliance


GOVERNANCE, RISK, & COMPLIANCE • CYBERSECURITY
Security governance: optimally managing digital risks
Security governance: optimally managing digital risks
Maintaining an optimal level of cybersecurity and information security is a great challenge and the consequences of not having an adequate strategy can have economic and reputational impacts on an organization.
It is important to establish a security governance framework based on regulations and best practices to align responsibilities, processes and guidelines within an organization and adequately manage digital risks.
At Axity we have specialized consulting services that adapt to the needs of organizations, increasing security levels with a methodology focused on risk prioritization, cost optimization and effective results through certified specialists.


Governance, Risk & Compliance services allow
Governance, Risk & Compliance services allow
Identify information security risks of confidentiality, integrity and availability, based on risk scenarios, processes, critical assets, owners, active users, vulnerabilities and threats detected. The risk analysis is based on the ISO 31000 Risk Management model and is complemented with the security controls of standards and frameworks such as ISO 27001:2013, NIST, COBIT, among others.
Through a gap analysis we can identify the state of maturity in relation to the controls dictated by standards such as PCI, ISO 27001:2013, C2M2, SOMM, among others.
Learn about the benefits of our Governance, Risk & Compliance service.
- To have a strategic cybersecurity plan aligned with best practices.
- Obtain indicators of digital risks outside the corporate perimeter.
- Minimize the impact on operations due to IT incidents.
- Engage the entire organization in the security culture as a corporate culture.
- Prioritize findings and investments.

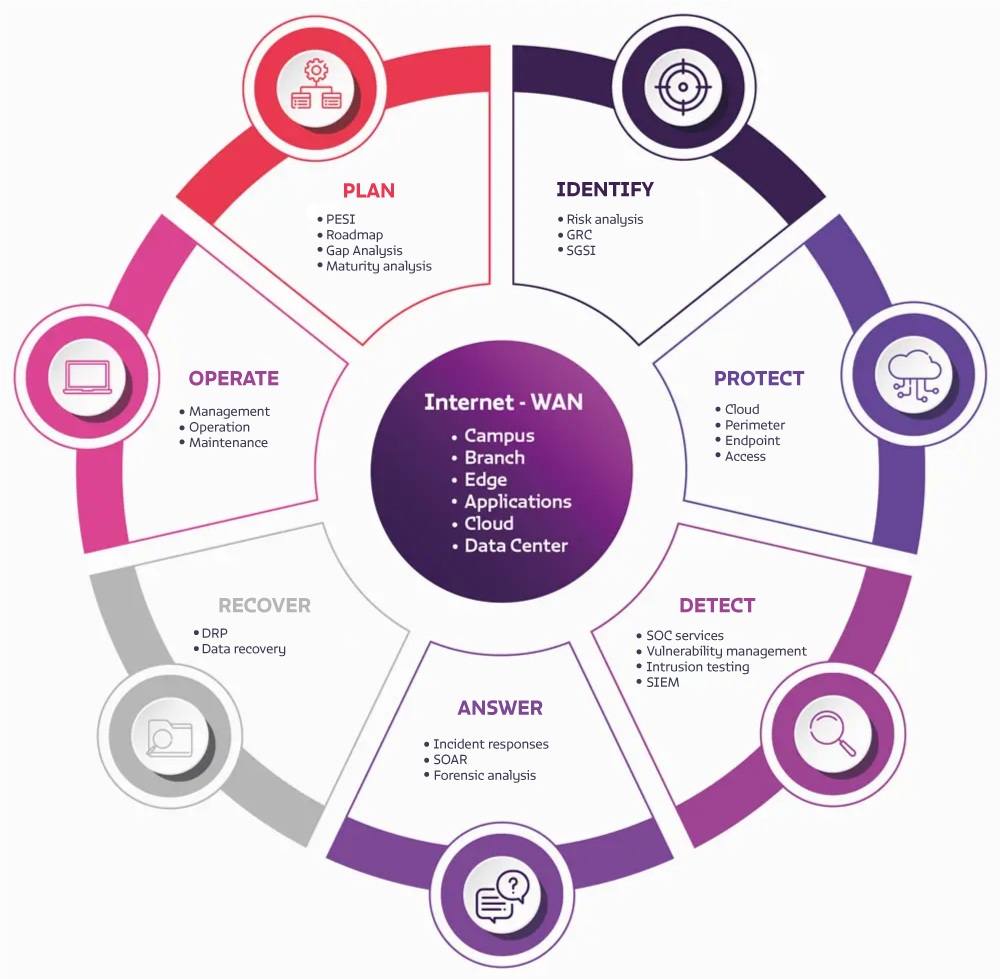
We implemented a solid solid Cybersecurity strategy
We implemented a solid solid Cybersecurity strategy
We have a wide range of products and services needed to implement a solid Cybersecurity strategy:
- Plan: goals, metrics, actions, infrastructure and talent.
- Identify: risk points.
- Protect: protection technology.
- Detect: detection technology.
- Respond: incident response strategy.
- Recover: operation and information.
- Operate: your entire cybersecurity process.
Technology partners






With Governance, Risk & Compliance, optimally manage digital risks and adopt a culture of cybersecurity in your company.
Complete the form and download
the e-book "How to implement a corporate cybersecurity strategy".
With Governance, Risk & Compliance, optimally manage digital risks and adopt a culture of cybersecurity in your company.
Complete the form and download
the e-book "How to implement a corporate cybersecurity strategy".