Managed
Security
Service
Experts in the administration, operation and monitoring of the networks and information of your entire business.

Managed
Security Service
Experts in the administration, operation and monitoring of networks and information for your entire business.
Managed


MANAGED SECURITY SERVICE • CYBERSECURITY
Managed Security Service;
AOM (Administration,
Operation & Monitoring).
Managed security services (MSSP) provide an alternative to organizations that can entrust specialized security companies with the responsibility to protect the networks and sensitive information that sustains their business by outsourcing the administration, operation and monitoring (AOM) of IT security solutions.
Managed Security Service Provider, is a service that solves the complexity of maintaining security capabilities with its own staff to address digital threats, because it requires mature processes, trained human talent and technology to address digital threats.
At Axity, through MSSP services, we manage, operate and monitor IT security controls of network (perimeter), endpoint, cloud, applications, among others, where manufacturers can be diverse, seeking to respond to digital requirements and managing incidents appropriately for our customers.


Managed Security Services
allow:
- Manage, Operate and Monitor (AOM) requirements in IT Security solutions.
- Support failures in case of incidents.
- Evaluate service performance and service levels.
- Have specialists by levels and security domains (network, endpoint, cloud, among others).
- Implement maturity actions and best practices of the managed technology.
Learn about the benefits of having a cybersecurity service provider:
Learn about the benefits of having a cybersecurity service provider:
- Tell us about the complexity of generating and maintaining cybersecurity capabilities within your organization, because it requires hiring, training and retaining human talent to maintain acceptable security.
- Reduction of failure times: we react with agility to incidents or even anticipate them.
- Experience and capabilities: we have a mature operation model in local and regional clients.
- Vision of the IT security posture, integrating multi-vendor technologies in the operation model.

We implemented a solid solid Cybersecurity strategy
We implemented a solid solid Cybersecurity strategy
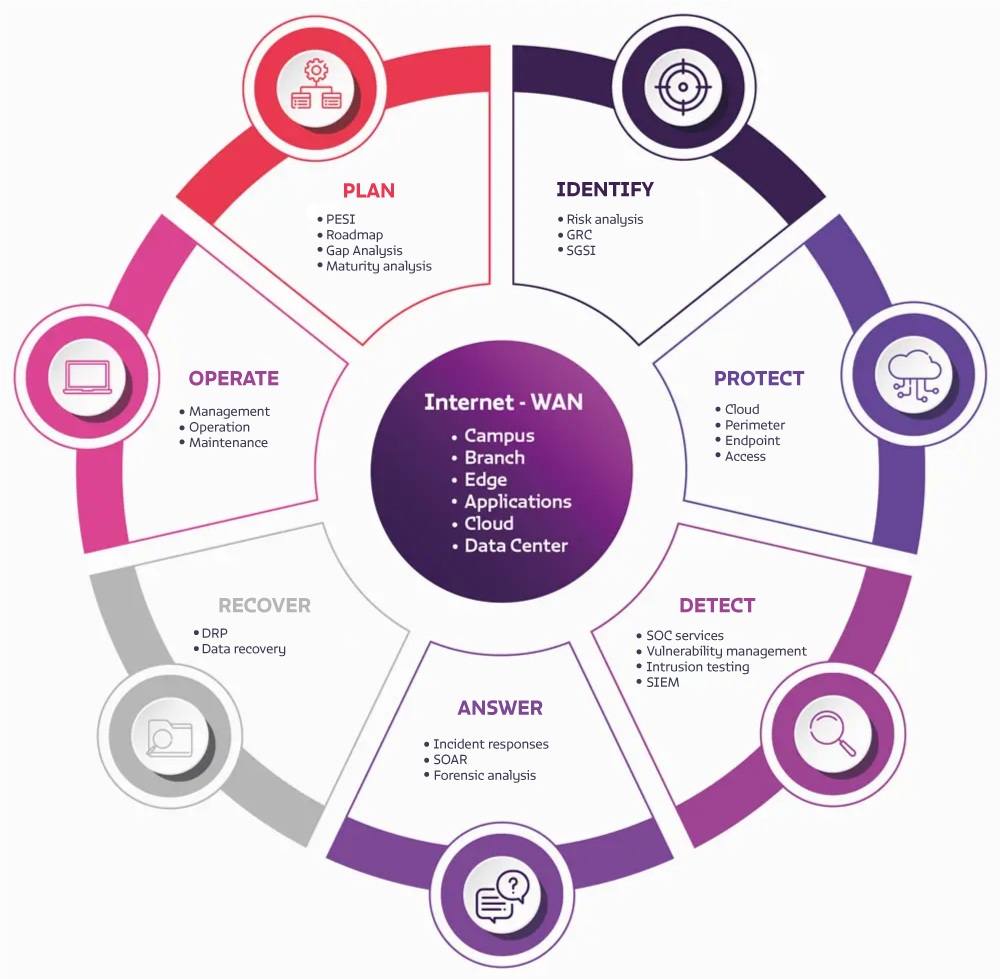
We have a wide range of products and services needed to implement a solid Cybersecurity strategy:
- Plan: goals, metrics, actions, infrastructure and talent.
- Identify: risk points.
- Protect: protection technology.
- Detect: detection technology.
- Respond: incident response strategy.
- Recover: operation and information.
- Operate: your entire cybersecurity process.
Technology partners
Managed Security Service






Solve the complexity of maintaining in-house cybersecurity capabilities.
Complete the form and download the e-book "How to implement an enterprise cybersecurity strategy".