SOC
CSIRT
We monitor and manage the infrastructure / cybersecurity software, to reduce exposure to incidents and contain them while minimizing the impact on your business.

CSIRT
SOC
We supervise and manage the cybersecurity infrastructure / software, to reduce exposure to incidents and contain them, minimizing the impact on your business.


CSIRT
CYBERSECURITY - SOC / CSIRT
Security Operations Centers (SOC) processes, technology and human talent
The high volume of data generated by IT components is a challenge for organizations to be able to identify information of security value, allowing decisions to be made at the time required to maintain the target security. The processes, technology and human talent of the Security Operations Centers (SOC) solve this situation, allowing to know at all times their security posture and anticipate digital threats that can generate consequences by the materialization of digital business risks.

From Axity’s Regional SOC, we monitor and manage the infrastructure / cybersecurity software of our customers, to reduce exposure to incidents and contain them effectively to minimize the impact on your business.

SOC services allow:
- Identification of cybersecurity events, correlation and automatic reaction with containment strategies.
- Permanent information on incidents and threats with Cybersecurity Newsletters.
- 24×7 attention scheme and from different geographies.
- Alignment with the best best practices (NIST / MITRE ATT&CK® / CyberKill Chain).
Discover the benefits of having a SOC / CSIRT
- Decrease in failure times and exposure to digital threats by detecting and mitigating security events.
- Anticipation of incidents by detecting attacks in early stages.
- High response capacity by specialized personnel in cybersecurity.
- Execution of best practices and threat trends by detection in other operations.

SOC
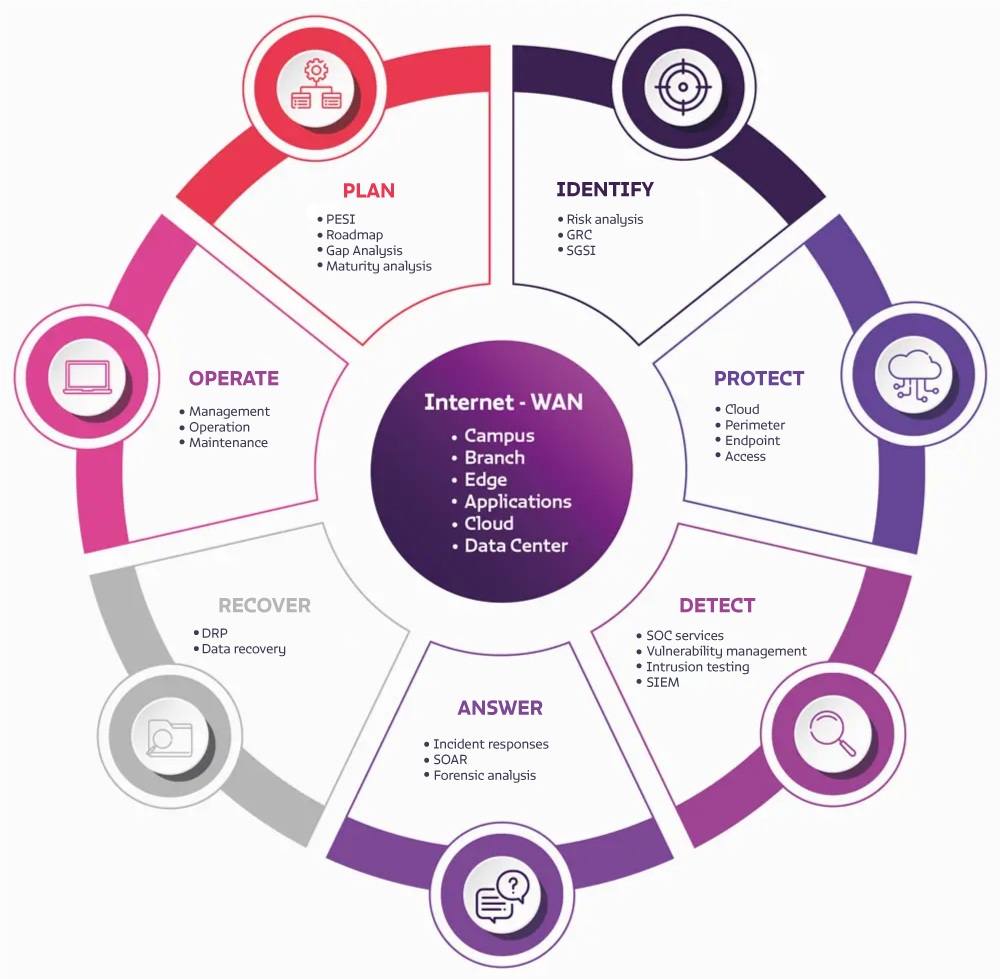
We implemented a solid solid Cybersecurity strategy
We have a wide range of products and services needed to implement a solid Cybersecurity strategy:
- Plan: goals, metrics, actions, infrastructure and talent.
- Identify: risk points.
- Protect: protection technology.
- Detect: detection technology.
- Respond: incident response strategy.
- Recover: operation and information.
- Operate: your entire cybersecurity process.
Technology partners






With SOC, reduce exposure to incidents and contain them to minimize the impact on your business.
Complete the form and download the e-book "How to implement an enterprise cybersecurity strategy".